$1,200. That’s how much someone is asking for a PlayStation Network account I’ve been investigating for the past few weeks. “Secure,” the person calls it, claiming the account will “never be touched” by the original owner again. “He won't be getting it back,” they claim. More than a thousand dollars? That’s a little rich for my blood, and so I counteroffer: $700.“Btc?” they respond, accepting my bid. (BTC refers to bitcoin. The majority of transactions like this take place using cryptocurrency; it’s generally harder, but not impossible, to trace.)
Advertisement
I didn’t purchase the account, of course. But I could—anyone could, if they only knew where to look. This account wasn’t on a shady market because someone was clumsy with their digital security. They had a strong password and two-factor authentication. When they were notified about problems with their account, they called Sony and asked for help.Despite all this, despite proving their identity over and over, they lost access to their PSN account, including any trophies earned or any games purchased. It was gone…well, sort of. The original owner no longer had access, but this person—the individual asking for $1,200 but who quickly and without hesitation dropped to $700—did.“Right now it feels like Sony’s system is protecting the people who stole my account and not me, the legit account owner of that account for almost 12 years,” said Justin, who asked to keep his identity and PSN name anonymous for reasons that’ll become increasingly clear.Sony did not respond to my multiple requests for comment about this story.To prove Justin owned the account in question, he forwarded me several PSN receipts with the username attached to the email, and various correspondence with Sony.Roughly a month after the launch of the PlayStation 3 and PSN, Justin did what a lot of people were doing: registered a username. There was nothing special about the username; it was the same one he’d been using online for years. And for a while, everything was normal. He played games, mostly single-player ones. Eventually, someone tried to gain access to his account, prompting an email from Sony thanking him for calling into customer service, but nothing more came of it. A fluke, surely?
Advertisement
It was not.Instead, it proved to be the opening shot in a ongoing struggle for Justin. This tug-of-war began in 2015, and escalated in recent weeks, where people would gain access to his PSN account, then he’d wrestle it back. Justin would add new security measures, figuring the digital wall would prove too high, or they’d get bored and move on—and they’d get it again.The moment Sony added two-factor authentication to PSN, Justin did, too.“I've had at least one or two instances,” he said, “where they got far enough where the two-factor prevented them, it stopped them. I was like ‘OK, that's what two-factor is supposed to do.’”Nothing is completely secure on the Internet, but there are steps you can take to make life harder for anyone trying to access your stuff. Two-factor authentication, where after entering a password the user is asked to paste a randomly generated code sent to an email account or device of their choosing, is one of the easiest steps one can take. It means an intruder requires access to your device or multiple accounts. It’s helpful, and it took far too long for Sony to add two-factor authentication to PSN, despite the service’s massive hack in 2011. Microsoft added two-factor to Xbox Live in 2013. It didn’t hit PSN until 2016, five years after the personal details of 77 million users were potentially exposed to hackers.Two-factor authentication is enough for most people, though increasingly, companies are offering more complex security layers, including dedicated authentication apps. (I use Authy.)
Advertisement
Until this point, what Justin was experiencing was annoying but tolerable. The two-factor notifications told him people were trying to gain access, but all he had to do was change his PSN password. Things changed last month, however, when he was getting ready for school.“I got a text message on my phone,” he said, “from the two-factor service saying ‘Your two-factor authentication has been deactivated. Please be careful, you don't have that protection.’ I won't say I'm a security expert, but I like to believe I'm security conscious. I knew I was screwed. I tried to log in, but it wouldn't let me log in, so I called Sony.”After proving he was the account owner, control reverted to Justin, but he was confused. Justin told me Sony’s customer service representatives couldn’t explain what happened, but noted they could flag the account as “sensitive or something”—he couldn’t remember the exact phrasing—which would invite extra scrutiny by future representatives.Justin pressed on. He registered a brand-new email account, one that hadn’t been associated with anything yet, and used the respected password management software LastPass to generate a 30-character password for his PSN account.“I would go longer but I hate manually typing it in the PS4,” he said.
“Right now it feels like Sony’s system is protecting the people who stole my account and not me, the legit account owner of that account for almost 12 years."
Advertisement
For the email address itself, however, he applied a 100-character, randomly generated password with two-factor authentication. After logging in, the name associated with the account (not the username) had changed. He didn’t take much note of it. Fear-something?“I changed it all back,” he said, “and I was like ‘OK, this happened before. It's never gotten this far, but it was probably a one-off. Sony said they'd keep an eye on it. I have a new email address. I have a new password. Everything should be fine."Narrator: It wasn’t.When Justin woke up the next morning, it was like Groundhog Day; another text message saying two-factor had been flipped off. After calling Sony, he learned the damage was more serious: whoever hijacked the account changed the email address it was associated with, punched in a new password, and set up their own form of two-factor for a phone number.When he tried to regain access through customer service, the said the account was now flagged as “protected.” Protected? This was different than “sensitive,” apparently. Protected turns on automatically, when the information on an account changes enough times to be considered erratic, and isn’t controlled by the representatives. Though the representatives confirmed Justin was the account holder, it was now, as Justin tells it, out of their hands. Another team was supposed to contact him in three days with more information.
Advertisement
During this phone call, something weird happened: someone texted Justin with messages he described “vaguely threatening,” promising to make things “worse” if he didn’t give up the account. (He deleted the text messages before I'd gotten in touch, when I asked him to start documenting everything.) If he didn’t give up the account, this person would make things worse at their job at Earthlink. They also made vague allusions to his wife and child.Here’s the problem: Justin never worked at Earthlink. Earthlink was his old internet service provider during the PlayStation 3 era, and there was an old Earthlink email address attached to a PSN child account he’d made for a reason he couldn’t remember. The hijacker, it seems, used these scant details to infer he worked at Earthlink, and had a family worth threatening.This was actually comforting to Justin. There was no family to be threatened. Plus, when he’d been thinking through the other ways someone might be getting access to his information—cloning his phone’s SIM card, a hidden keylogger tracking the movements on his keyboard, a fully compromised email account—it was potentially much worse. Had that been true, though, why hadn’t anyone used his credit card? Accessed a website that could do more financial damage than his lowly PSN account?The fact that two-factor was disabled on Justin’s account is an important, complicating point. In order to disable two-factor, you’d theoretically have to have full access to the account, which also means access to the email (or device) the two-factor code is being forwarded to.
Advertisement
In such a case, wouldn’t the hijacker have access to more information than the misleading details on the PSN account, such as an old email address? Something wasn’t adding up.Who, then, was disabling two-factor on his account? A key piece of evidence to consider: Sony had told him someone had called about his PSN account a whopping 12 times in the past 48 hours. A few of those were Justin, but the vast majority of calls were someone else.“I assume he's wasting an hour or two [on the phone with Sony], at least?” said Justin. “It takes me half an hour to sort it out, and I have all the information. [laughs] So I'm just going off how long it takes me, and I hope it takes him at least as long. I hope he's not calling up and getting it done in 10 minutes.”A potential culprit, then, is social engineering, a now-pervasive technique where someone uses pieces of information to trick someone, usually customer service representatives, into gaining access to another person’s account. This would explain the volume of phone calls. If you don’t succeed with one representative, call back and see if another will be more willing.Though Sony asked Justin a series of personal questions to re-establish identity—the primary email address on the account, serial number of his first console, first city he logged in from—they also asked for details, like recent purchases, that could be found by punching in the account into any number of websites and seeing what trophies had recently unlocked.
Advertisement
(I asked multiple individuals who recently spoke with Sony’s customer service over similar issues, and several mentioned Sony asking for recent purchases as one of their identity metrics.)Once you know one piece of information, it’s not difficult to start punching that into Google and find other pieces of information that might be just enough for a more lax representative.Whatever happened, the end result was the same: When Justin finally heard back from Sony, they didn’t apologize and promise to protect the account. Instead, they said it—an account Justin has had for more than 12 years, with a history of trophies and purchases—was gone. There was nothing he could do, no process to appeal, no way to get any of his games back.“I couldn't get any confirmation on if the person who ‘hacked’ it is locked out, but I sure as shit am,” he said. “From what I can gather I have lost that account and Sony can't or won't do jack shit about it. If the person who stole it is also locked out that is one thing, but I couldn't get a concrete answer on that piece of info.”That’s when I went looking for answers, and how I’d end eventually end talking someone down from a $1,200 asking price for Justin’s account to only— only—$700. My first tip came from one of Justin’s friends, who, in a fit of frustration, looked up Justin’s account on PSN, and found someone was actively using it, and had changed a bunch of information on it.
Advertisement
Importantly, it listed an active Twitter account in the “about me” section of the profile, an account that featured a (now deleted) screen bragging about access to Justin’s PSN name:
A reply mentioned another account, who also bragged about nabbing Justin’s PSN name.
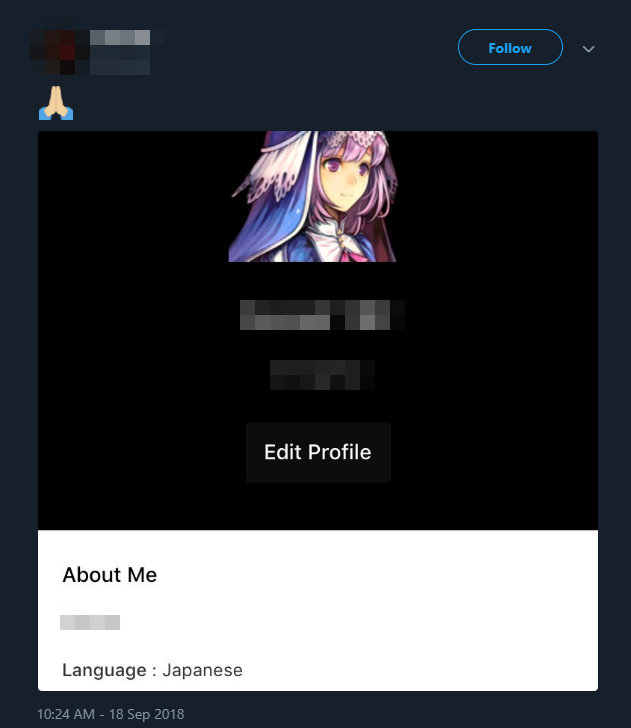
When I contacted the first person, who had open direct messages, they pleaded ignorance, and repeatedly claimed it was their account. “What makes you believe the account was stolen?” they asked. Not long after, they locked their account—and deleted the screen shot.It’s at this point that I contacted a source close to the hacking and piracy community, who pointed me towards a popular message board for sharing, selling, and buying “OG,” aka original, accounts across a variety of platforms, including Fortnite, Snapchat, Steam, Twitter, and, of course, PlayStation Network.I’m declining to name the message board due to the sensitivity of the information on it.On the board, there are guides to “secure” a PSN account in case “someone attempts to get the account back,” albeit with the important caveat “there’s no way to secure a PSN 100%.” One of the key suggestions is to quickly change the account to Japanese, which you’ll notice happened with Justin’s account. One of the screen shots listed the language as “Japanese.”It was easy enough to register an account on this message board. There’s no vetting process. You also don’t have to pay anything to search the database, either. Once I was in, I plugged Justin’s PSN account into the search field and voila. There was a thread selling his username for $1,200.
Advertisement
In the thread, the seller promises the account is “secure.” There’s scattered and disputed discussion about whether the account has been sold before, but the seller claims it hasn’t. Importantly, there’s a discussion over whether the “og owner,”—Justin—could regain access.“He won’t be getting it back,” argued the seller.“Are you going to have a pull war with him or what,” asked another user.“Not really a pull war when he not gonna pull lol” retorted the seller.Pull war is a reference to the cat-and-mouse game Justin had been playing with this person, or possibly someone else, and Sony’s customer service department. The seller was boasting there’s no way it’ll switch hands, a claim bolstered by what Justin was told by Sony: the account is lost. In this case, though, it’s not “lost” because Sony locked it down, it’s lost because the user apparently had pulled enough tricks to make sure it’s out of Justin’s hands.The seller even referenced the text message conversations he had with Justin:
Soon after, another user vouches for the seller’s authenticity, but is called out by someone as being a duplicate account for the seller—a violation of the board’s rules. He’s now banned, amid speculation from other users the seller cannot back up claims of securing the account.“Use your brain a lil bit,” said another user. “There are ways to make sure og owner doesnt get it back. If you dont know then you dont.”
Advertisement
The other user concedes the point.The seller continues to bump the thread— it’s been on sale for nearly a month—but no one’s biting. That’s when I decided to send a message, asking for proof about the account. He agrees to add me as a friend on PSN, and after registering a new account, I send a request.Jackpot.
A screen shot from a burner PSN account I made.
You’ll notice we’re now friends, as evidenced by the “your friend” note in the corner. The avatar is the same as the one referenced in the screenshot from Twitter a few weeks back.This is when I decided to negotiate. Nobody had bought the account at $1,200, so maybe he’d go a little lower. Like I mentioned, I picked $700 out of thin air, thinking we’d settle somewhere in the middle, but they immediately agreed to my asking price. No negotiation.“No one actually pays real money for accounts, so I bet he’s thrilled,” said the hacker who’d tipped me off to the forum in the first place.I haven’t paid any money for the account, of course. Nor has anyone else.More than likely, Sony itself is a victim of a clever social engineering scheme, in which a user, or series of users, repeatedly spammed their representatives, until it found someone willing to accept the limited information they did have, and calculated the system would eventually lock the account in their favor. Even a "failed" social engineering attempt can be a success, if the person calling comes away with new information about the account. Every company in the world can fall victim to social engineering, as there are no true fail safes. But Sony’s setup seems especially ripe for it.
Advertisement
Why didn’t the system get flagged as “sensitive” sooner? Why can a user flip off two-factor authentication over the phone? How can an account get abandoned, when it’s still active?There are ways Sony could have prevented this from happening.As I mentioned before, Sony did not respond to my request for comment about this story. They didn’t respond to my request for comment in 2017 when I investigated the shady world of PSN account resellers, either. PSN has a long, troubled history of putting their users in compromising situations. There are always exceptions, and no digital security is completely safe, but when someone follows all the rules, shouldn’t the company go above and beyond?In this case, Sony most definitely did not—at first, anyway.Though Sony did not officially respond to me, a few days after being alerted to the situation, in which I outlined everything that had happened to Justin’s account, he got a phone call. A week after Sony told Justin he was screwed, he was magically being handed the account.“Sony promised that they were going to set it up so no reps could make any changes,” he said, “but they are still investigating how this happened.”Sony did not respond to my request for comment about this new development.There’s evidence the seller truly did believe they had the account “secured.” There was a new name and address associated with the account, and $15 in credit had been added. The seller even purchased some new games. This was an account someone intended to use, or allow someone else to use, if they’d agreed to an asking price of $1,200. (Or, uh, $700.) It’s also possible the purchases were made to establish a new purchase history, one of the identity metrics Sony’s customer service uses to establish who is the owner of an account.Justin was also given a specific phone number to call in the future, if he has new problems.“I have my account all set up now,” he said. “We shall see how well Sony can protect it.”As for the seller, I called their bluff and asked for evidence they still had the account. They demurred, accused me of trying to waste their time (fact check: true), and asked for their money. They'll have to keep waiting.Follow Patrick on Twitter. If you have a tip or a story idea, drop him an email: patrick.klepek@vice.com.Have thoughts? Swing by Waypoint's forums to share them!
