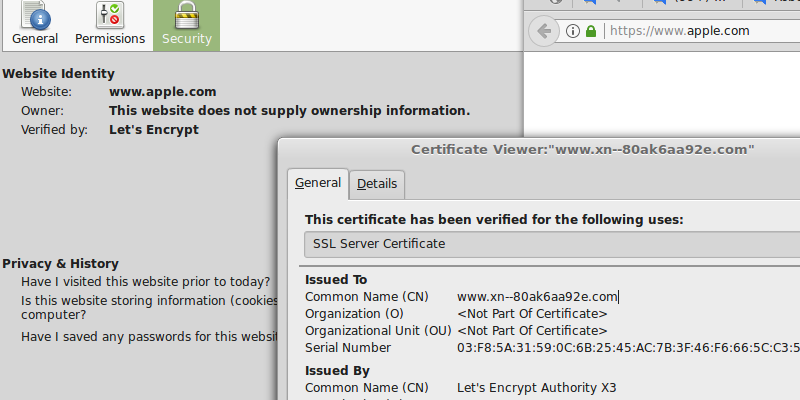
Well, think again. At least if you are using Chrome or Firefox. Don’t believe us? Well, check out Apple new website then, at https://www.apple.com . Notice anything? If you are not using an affected browser you are just seeing a strange URL after opening the webpage, otherwise it’s pretty legit. This is a page to demonstrate a type of Unicode vulnerability in how the browser interprets and show the URL to the user. Notice the valid HTTPS. Of course the domain is not from Apple, it is actually the domain: “https://www.xn--80ak6aa92e.com/“. If you open the page, you can see the actual URL by right-clicking and select view-source.
So what’s going on? This type of phishing attack, known as IDN homograph attacks, relies on the fact that the browser, in this case Chrome or Firefox, interprets the “xn--” prefix in a URL as an ASCII compatible encoding prefix. It is called Punycode and it’s a way to represent Unicode using only the ASCII characters used in Internet host names. Imagine a sort of Base64 for domains. This allows for domains with international characters to be registered, for example, the domain “xn--s7y.co” is equivalent to “短.co”, as [Xudong Zheng] explains in his blog.
Different alphabets have different glyphs that work in this kinds of attacks. Take the Cyrillic alphabet, it contains 11 lowercase glyphs that are identical or nearly identical to Latin counterparts. These class of attacks, where an attacker replaces one letter for its counterpart is widely known and are usually mitigated by the browser:
In Chrome and Firefox, the Unicode form will be hidden if a domain label contains characters from multiple different languages. It is possible to register domains such as “xn--pple-43d.com”, which is equivalent to “аpple.com”. It may not be obvious at first glance, but “аpple.com” uses the Cyrillic “а” (U+0430) rather than the ASCII “a” (U+0041). The “аpple.com” domain as described above will appear in its Punycode form as “xn--pple-43d.com” to limit confusion with the real “apple.com”.
So far so good, the browsers filters these types of counterpart character substitution. But there’s a catch. It appears that the mitigation fails when all characters in the URL use the same alphabet. The domain “аррlе.com” as in the website shown before, registered as “xn--80ak6aa92e.com”, bypasses the filter by using only Cyrillic characters. One can understand why a developer may have chosen this behaviour, nevertheless it presents a problem, as demonstrated.
This affects the current version of Chrome browser, which is version 57.0.2987 and the current version of Firefox, which is version 52.0.2. This does not affect Internet Explorer or Safari browsers. If you are using Firefox, you can switch off the Punycode translation in about:config by changing network.IDN_show_punycode to true. If you are using Chrome, you’ll have to wait for the update. Or manually check the HTTPS certificate in HTTPS enabled websites.
Aren’t you just tempted to register a domain to go and phish the phishers?
[Thanks chrisatomix]















This is already fixed in v58+ of Chome, just released.
I have just updated to Version 58.0.3029.81 (64-bit) and still showing the fake URL. On windows 10
Any ideas?
Use Firefox?
Still not fixed as of Firefox v53.0
Restart Chrome after updating. Worked for me with Chrome Version 58.0.3029.81
Had to clear my cache after updating before update worked.
Tangential: I have been noticing much more aggressive caching, or at least, much less effective cache updating on chrome lately. Anyone else noticing this/considering this?
Yeah, it is worse than last update. I usually load several tabs and then view them offline to conserve battery life and data. But then half the pages attempt to reload and it’s gone.
Hackaday works fine though.
updated and restarted, fixed
Thank you for posting this!! I just went and updated my chrome…
Thanks. Manually patched my browser.
+1
So reported this to the security @ firefox?
Firefox has security?
Yes. The ‘s’ in Firefox stands for “security”.
+1
Firef*cks? Look, there’s the ‘s’ of security.
Bruce Schneier has been warning about this kind of stuff for at least a decade. I’m surprised it’s taken this long to be seen in the wild.
I was about to say this. I remember this type of attack making waves maybe like a year ago, but it’s been an ongoing thing for a while now. Glad it’s getting “sorted out”, I guess.
It’s been recommend for at least 3 years to set the punycode option in Firefox when dealing with IDN. And the attack using IDN has had a working example since 2010, and it was theorized a few years before that. (before IDNs even went online!)
It’s not clever at all, it’s just sloppy on the part of ICANN and IETF.
Thanks, I’m using firefox and changed the config as suggeted.
I see it a lot of this in email malware/spam that appears to originate in russia and china and trying to impersonate banks and financial institutions…at least on our servers.
I’d like to see an article here on the chinese malware bots hitting web servers with url requests looking for files containing names like /GXHLGSL.txt
I’ve even noticed google now searching for the same strings.
Botnet C&C URLs, or maybe “flag” files from some kind of botnet? Also, Google bots will also visit links that Chrome users visit.
They are looking for open proxies.
The tech ages moves so fast that this article is already obsolete! My Chrome just updated to 58.0.3029.81 and shows the “xn--80ak6aa92e” string in the URL box.
Same. I saw the article, tried the URL, and the exploit worked. Saw your comment, went to Chrome’s “About” page, and it was already in the process of downloading an update. Now that I’ve restarted Chrome after the update, it shows the correct URL (xn--80whatever).
+1
ffs. Why is this not fixed yet. We shout and scream at users to check urls before clicking them, etc. And yet we let shit like this through.
The only sure fix is to not support IDNs. Other proposals are not effective. And you know those browser guys are chicken sh*t and won’t remove standardized misfeatures.
Mozilla Thunderbird email client as well as Chrome sure does fall for it.
Would this trick a password manager? I’m guessing not, in which case I don’t need to “think again” quite yet.
Of course when someone zero-days my password manager…
You’d see it and go “hrm, why did my browser forget my password? Oh well, I enter it in again”
Thanks, I’m using firefox 52.0.2 and changed the config as suggeted.
This “bug” has come up before and Firefox devs decided that this particular case couldn’t reasonably be filtered. https://wiki.mozilla.org/IDN_Display_Algorithm
There’s a reason that firefox is leaking user base at a rate of knots… this kind of attitude can’t help either.
Also the fact they dropped the ALSA backend forcing people to FalseAudio or another browser.
They could at least have an option selection of, “Enable ALSA (Stereo)” and, “Enable PulseAudio (Surround)”, that would help those who’s not got a mid-end laptop manufactured 5 minutes ago and theirs may not handle PulseAudio smoothly.
Also, seems though soundcloud has moved to Flash instead of the more compatible/widely supported HTML5, just because Adobe has resurrected support for Linux users (Though it gives the lazy ones in the Linux users pond a kick up where the sun doesn’t shine).
Youtube still sticking with HTML5 for now it seems.
Oooo will have to check renewed support for flash out… Couple of flash heavy sites I have to rely on, and the older machine I sandbox them on is a bit doggy. Wondering if lubuntu will be better now
V25 for NPAPI and PPAPI as separately supplied downloads straight from the adobe website(Looked at 32bit linux support though, not sure if more options for 64…)
Just updated said flash player,
However it claims to require several generations of glibc newer than the one I have, so –force –nodeps on the RPM and a manual copy of the .so into the firefox addons. Then another addon to force youtube to not serve me HTML5 (So flash works instead). Now I have sound on an ALSA only configured Debian.
Addons to work around firefox feature removal all over again, they should remove the page viewing pane next because who needs to see websites anyway!
Also my battery time at 20% on firefox has gone down from 1h 45mins to 28mins!!!! just by using flashplayer instead of HTML5!
Though I remember underclocking (switching to the lowest freq multiplier: 800Mhz and makes a BIG difference in runtime extending) saves battery and heat without causing stutter in flashplayer played videos, even though the CPU utility goes 100%, but that was time ago (flasplayer V11 era).
Time to do some rethinking of my energy usage and OS configuration if I want that 3+ hour use away from mains, the biggest reason I haven’t upgraded my OS to the newer Debian 8.x as I had less runtime under such a newer Debian(GNU)+Linux OS, albeit they were unconfigured live CD ISOs on USB.
Their decision to depend on the thing formerly known as PolypAudio is why I’m leaving FF after being extremely satisfied from Phoenix 0.9 up to just before the Australis fiasco, when I learned to love Classic Theme Restorer, which is nearing its EOL because the Mozilla devs are now also ripping out the spinal cord lots of customization extensions need. Really rather sad. Ladies and gentlemen, the “Free Web”
P.S. ALSA isn’t dropped outright, just the official binaries are nerfed. You can compile it yourself with ALSA and JACK and *no* FoolsAudio, though it really helps to be on any distro that automates that
Firefox 31.6.0 on OpenIndiana 151_a8 shows the URL correctly at the bottom left of the browser window. I *always* check links in blog posts and emails to see where they point.
dadja notice gmail clickjacks all links with javascript? the href shown at the bottom is not where the link goes to. I only noticed when I added a 301 blocker.
You should do a “show source” for the Google home page.
I wondered why the simple minimalist looking Google.co.uk page used considerably more battery than hackaday.com (With all adverts white-listed and loaded).
Config change worked on FireFox 52.0.2 and Thunderbird 45.8.0 , thanks.
Chrome 58.0.3029.81 didn’t seem affected. This is all under Xubuntu 14.04
Opera also seems to be affected by this.
Opera is Chrome with added spyware. Qihoo 360 Technology Co. Ltd. bought the company and they’ve been caught installing monitoring software into other software packages, it’s only a matter of time before they mess with your browser.
Reporting from Pale Moon (FireFox derivative), it displays the punycode on the URL… Looks like it’s mostly the base FF and older browsers that are “vulnerable”.
I tested v25 & v26 and neither of those appear to be affected by this either. Both of them show the ‘xn--‘ style domain.
I did notice one oddity. The shortened entry on the front page shows and links to the Apple URL. The extended entry on the blog page and the article itself show and link to the ‘xn--‘ style domain.
Using Palemoon v27.1.2 and I see just a strange URL that seemingly does nothing, also hovering over said link shows the xn-etc.dom style link in the status bar. I seem to be unaffected, however I’ll re-read this article a few times and try the linked pages (Info sources, not the fake website) before concluding.
So I clicked the link and got what appeared to be the Apple website. Does this mean I’m vulnerable?
you are more vulnerable than words could ever convey. step away from the keyboard.
if you get the actual apple website, then no, but if you get http://www.apple.com in the URL bar and it is an odd info page instead, then yes, vulnerable.
The whole point is it’s a site that isn’t what it says it is in the URL, imagine this being done to create a false paypal page, etc etc. It tricks you into feeling secure after you manually look at the URL bar, except the URL bar lies to you!
I noticed that clicking the link from the homepage of hackaday led to the real apple.com,but the one in the article did not. Did anyone else have that?
Yes, I looked at the source for the main page and its apple.com, but when you go to the article proper its the unicode attack site in the body link.
Funny, I’m running Firefox on Linux Mint right now and it’s using a serif font so the capital I stands out but it still is showing the “spoofed” url.
same for me (xubuntu1604)
HAD posts outdated Information sometimes
Thank you!
Firefox ESR 52.1.0 shows apple.com but the ‘L’ looks really strange, like gray instead of black.
how the hell did apple not buy out the domain appie.com?
On Safari 7.0.6, the link from the front page goes to the real Apple Inc. website. To visit the phishing site, I have to click through to the article, and follow the link from there.
The Status bar shows the URL when I mouseover, and that is correct without visiting the page (it shows only the ASCII URL, not Unicode).
Same thing here, the front page link is different than the one in the article.
While I can see that showing Punycode in the URL is a better option for security, doesn’t that make the Web very Anglocentric again? I mean why bother registering a domain in real Katakana or whatever, if it is just transformed into xn--somethingUnrecognizable at the URL bar?
This is probably why Firefox stands by their original implementation, because an all-Cyrillic URL is probably just a Cyrillic website, so why encode it?
Now is the point where I would start bashing on the Unicode Consortium (again) but ai will take the day off instead.
I totally agree. I bought the domain http://ƙeith.com/ because I liked the look of the ƙ vs just a normal k and it’s annoying that it gets decoded by browsers.Probably just going to let this domain expire as a result. I was not aware that browsers did this till I registered that domain.
However speaking Katakana. I do like this domain all katakana so no browser decoding. http://キース.コム/
Also what about character sets that are used in multiple languages.
I will add one more sad thing is that ƙ is part of the Latin character set https://en.wikipedia.org/wiki/Latin_script_in_Unicode
Perhaps the sensible approach is to vary by TLD; an all-cyrillic domain is okay in .ru, but should be flagged and displayed as ascii in .com?
I could not red the Katakana anyway. Cyrillic or Greek letters I could try to interpret, or at least try to remember. But if the URL is Cyrillic, probably the text is also :-( I would not understand it. So for me the solution to turn off Punycode interpretation is a good one.
This is exactly, right there, why companies like Santander who refuse to pay up when their customers get phished, should be shut down or at least have military grade security.
Or just do what I suggested and ban online and phone banking until security can be guaranteed.
“ban online and phone banking”
That’s blasphemy !!! Do you realize how many people we would put out of work ? All the “IT security” people, the mindless/numb/useless droids on the ‘customer service’ 1-800 lines, why it would be a cataclysm of biblical proportions! (sort of like the scene out of “American Gangster” – where Russell Crowes detective character says “they don’t want it to stop – the day dope stops flowing into this country, a hundred thousand people lose their jobs – the prison guards, the lawyers, the cops”)…..
Sarcasm aside, your suggestion would be the perfect solution to the entire identity theft, cyberfraud problems we now have (all because of the need for ‘convenience’). We typically never heard of such issues “back-in-the-day” when the only way to transact business was, you walk into the bank, talk to the teller/manager, etc – and if necessary show them some form of ID – all the while, you’re being recorded on surveillance videos. It was a – eh, reasonably, secure type of deterrent to any fraud attempts.
“I give him double O status, and he celebrates by shooting up an embassy, is he deranged? in the old days an agent would have sense enough to defect. God I miss the Cold War”…….”M” (many other relics from that time we all miss – no internet banking for one !)
I don’t think there is a character in cyrillic script that is a homograph of latin lower case “L”.
Anyway, I’d say it seems that the problem goes back to Unicode itself. One character shape should had never been assigned two different representation codes. We were so concentrated on meaning and completely forgot about significance of form. Proper handling of international text just shouldn’t pretend that homographs don’t exist, and instead treat latin, greek, and cyrillic alphabets as one monolithic union of graphemes, or at least extract their intersection and use it as one single set. There should be another mapping, hierarchically above the grapheme set, which define individual alphabets.
FF50 here, although the link renders as “apple” when I mouseover the link the status bar uses a different font that renders the ‘l’ much more clearly as more like a ‘1’. Yeah, not perfect, but spottable.
Mind blown, and I’m a web developer.
amazing find just updated.
Upgraded to FF 53.0 while reading this article. Mouse-over still shows apple.com but clicking the link brings up a warning page that says: “This may or may not be the site you are looking for! This site is obviously not affiliated with Apple, but rather a demonstration of a flaw in the way unicode domains are handled in browsers.”
Darn! I was really hoping to see some of Joe’s art for the opening picture!
the example looks more like it says appie than apple.
However i am quite sure there is other domains that is actually at risk. or other similar letters.
How do I make my own Web page that tests this vulnerability locally? Having to go to a page in the “wild” is dangerous IMO (i.e., the example page linked from this HaD post is now a Honey-Pot!)
Chrome 58 works well for my Windows 8.1.Thank you for that info!
IE is safe IE is life
when browsing pages/links i do not trust, i usually right-click and hit copy-link-location, then i paste URL links into a program, it allows pasting a link for inspection in a simillar way to notepad and when i hit ok it loads the URL into selected browser AFTER i inspect (andor edit) the link, in this case it gave me https://www.?????.com as the address… hmmm i wont be hitting ok on THAT one any time soon!
with all the hacking going on lately, im just wondering if maybe someone hacked into hackaday/wordpress and posted a fake article??? i mean taking down the site or copying all the sin numbers is bad but a fake article might go unnoticed…
maybe everyone that actually clicked the link needs a primer on what exactly phishing is… its a system to trick you into clicking this one weird link… you clicked a link you KNEW was fake… i dont feel the least bit sad knowing what MIGHT have happened, if H.A.D. had been hacked into, after all, it admitted it was a fake link…
im not saying it was a BAD link, what im saying is you should be more careful of what you click.
and as always, remember, that the FROM field on an email is actually OPTIONAL, its just that when its left blank it is rejected by the recipient, but if it’s fake, it goes through!!! when xyz123@dfgh3341.com is black-listed, they will register xyz123@dfgh3342.com and the chase continues.
Outlook Mail Client and Gmail is vulnerable as well. Our PoC and article: https://ciberseguridad.lamula.pe/2017/04/22/ataque-de-phishing-imperceptible-con-unicode-tambien-afecta-clientes-de-correo-electronico/delphins/