A grey-hat hacker going by the name of Stackoverflowin says he's pwned over 150,000 printers that have been left accessible online.
Speaking to Bleeping Computer, the hacker says he wanted to raise everyone's awareness towards the dangers of leaving printers exposed online without a firewall or other security settings enabled.
Automated script behind the "attacks"
For the past 24 hours, Stackoverflowin has been running an automated script that he wrote himself, which searches for open printer ports and sends a rogue print job to the target's device.
From high-end multi-functional printers at corporate headquarters to lowly receipt printers in small town restaurants, all have been affected.
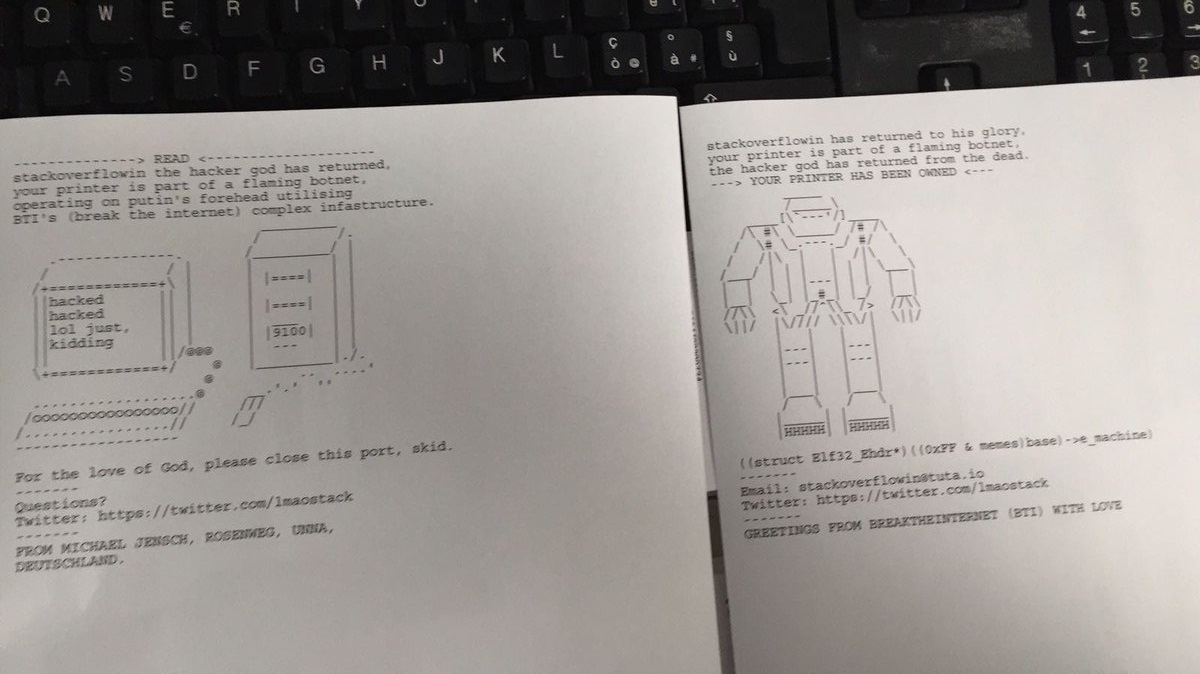
This is the latest version of the message spewed out via people's printers:
stackoverflowin the hacker god has returned, your printer is part of a flaming botnet, operating on putin's forehead utilising BTI's (break the internet) complex infrastructure.
[ASCII ART HERE]
For the love of God, please close this port, skid.
-------
Questions?
Twitter: https://twitter.com/lmaostack
-------
A first version of the message included ASCII art depicting a robot, and also listed the hacker's email address. The second (latest) version of the message includes ASCII art depicting a computer and a nearby printer, as depicted below.
Stackoverflowin's actions haven't gone unnoticed, and many people went online to ask for details, such as HP's official support forum, StackExchange, Spiceworks, local forums, Reddit, YouTube, and Twitter (tweets available at the end of this article).
Multiple printer brands affected
Users reported multiple printer models as affected. The list includes brands such as Afico, Brother, Canon, Epson, HP, Lexmark, Konica Minolta, Oki, and Samsung.
Stackoverflowin told Bleeping Computer that his script targets printing devices that have IPP (Internet Printing Protocol) ports, LPD (Line Printer Daemon) ports, and port 9100 left open to external connections.
The script also includes an exploit that uses a remote code execution vulnerability to target Dell Xeon printers. "This allowed me to inject PostScript and invoke rouge jobs," Stackoverflowin told Bleeping about the RCE vulnerability's role.
It was only a joke
The hacker, who says he's done his share of security work, claims his intentions were all good.
"Obviously there's no botnet," he says. "People have done this in the past and sent racist flyers etc.. I'm not about that, I'm about helping people to fix their problem, but having a bit of fun at the same time ; ) Everyone's been cool about it and thanked me to be honest."
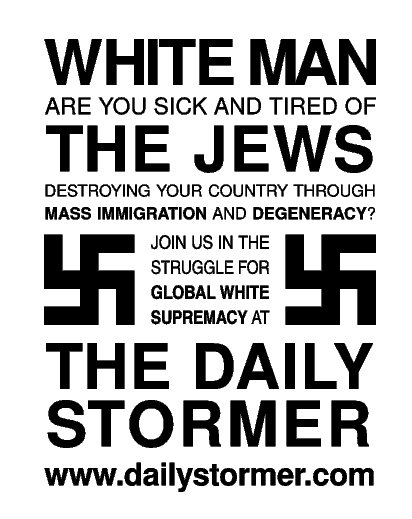
The incident Stackoverflowin is referring to happened in March 2016, when famous hacker Weev has made thousands of Internet-connected printers spew out anti-Semitic messages.
A report released last week reveals the overall sorry state of printer security. Researchers argued that printers could be used as entry and pivot points when attacking corporate networks.
Below is a collection of tweets and images from the people that had printers spew out Stackoverflowin's message.
@lmaostack lol? pic.twitter.com/cjvEstn55t
— Kenshin el Manco (@d_kenshin) February 4, 2017
@lmaostack yall got me fucked up!!! pic.twitter.com/fJi1beoSU7
— lindsey (@lindsucks) February 3, 2017
@lmaostack um why are u hacking my printer at work pic.twitter.com/OpocSpRutm
— Summer Gale Fuss (@summer_fuss) February 4, 2017
@lmaostack memed on in the morning pic.twitter.com/xZtTTqRsEO
— stef. (@sixthimpact) February 4, 2017
I'm honestly just impressed with these printer hacks more than anything. Thanks for entertaining me during my double shift @lmaostack pic.twitter.com/EzFXmqmDeo
— Faith Kennedy (@faithers99) February 4, 2017
@lmaostack LMAO! <3 can u send someone of Tweety? on my country we love tweety LOL pic.twitter.com/q70pZaByN8
— Remigio Isla (@lttle_wolf) February 4, 2017


Comments
Zone_86 - 7 years ago
and?